Openbravo Issue Tracking System - Openbravo ERP |
| View Issue Details |
|
| ID | Project | Category | View Status | Date Submitted | Last Update |
| 0014858 | Openbravo ERP | C. Security | public | 2010-10-12 01:47 | 2022-02-01 08:08 |
|
| Reporter | cmlh_id_au | |
| Assigned To | Triage Platform Base | |
| Priority | high | Severity | major | Reproducibility | always |
| Status | acknowledged | Resolution | open | |
| Platform | | OS | 20 | OS Version | Community Appliance |
| Product Version | | |
| Target Version | | Fixed in Version | | |
| Merge Request Status | |
| Review Assigned To | |
| OBNetwork customer | No |
| Web browser | |
| Modules | Core |
| Support ticket | |
| Regression level | |
| Regression date | |
| Regression introduced in release | |
| Regression introduced by commit | |
| Triggers an Emergency Pack | No |
|
| Summary | 0014858: Cross Site Scripting (XSS) - Reflected - UserRoles _Edition.html - "inpadUserId" Parameter |
| Description | The value of the "inpadUserId" Parameter is not validated and/or escaped during the HTTP GET Request of /openbravo/User/UserRoles_Edition.html and hence is vulnerable to Reflected Cross Site Scripting (XSS) |
| Steps To Reproduce | OpenbravoERP-2.50MP22-x86.vmware.zip was used to reproduce the Reflected XSS
1. Substitute the value for [FQDN] below and then copy and paste the following URL into Firefox after authenticating to OpenbravoERP VM:
http://[FQDN]/openbravo/User/UserRoles_Edition.html?inpAccessLevel=6&Command=&urlwin=UserRoles_Edition.html&inpTabId=121&inpTableId=157&inpadUserId=100%22%3E%3Cimg%20src%3da%20onerror%3dalert%28%27XSS%27%29%3E&inpkeyColumnId=AD_User_Roles_ID&inpadUserRolesId=&inpKeyName=inpadUserRolesId&inpwindowId=108&inpParamSessionDate= [^]
2. A Javascript Alert Box will display "XSS" as per the attached screenshot. |
| Proposed Solution | Validate and escape the value of the "inpadUserId" Parameter on the server side i.e. prior to the Javascript being executed by the web browser.
|
| Additional Information | |
| Tags | No tags attached. |
| Relationships | |
| Attached Files |  Cross_Site_Scripting_(XSS)_-_Reflected_-_ UserRoles_Edition.html_-_inpadUserId_Parameter.jpg (75,472) 2010-10-12 01:47 Cross_Site_Scripting_(XSS)_-_Reflected_-_ UserRoles_Edition.html_-_inpadUserId_Parameter.jpg (75,472) 2010-10-12 01:47
https://issues.openbravo.com/file_download.php?file_id=3216&type=bug
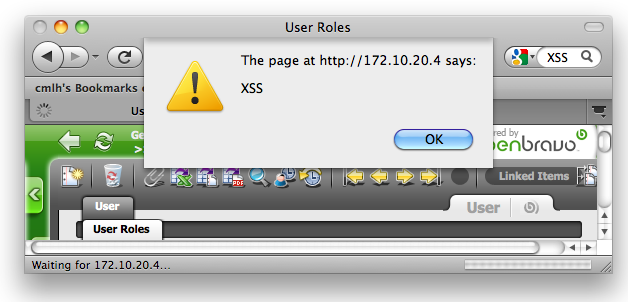
|
|
| Issue History |
| Date Modified | Username | Field | Change |
| 2010-10-12 01:47 | cmlh_id_au | New Issue | |
| 2010-10-12 01:47 | cmlh_id_au | Assigned To | => alostale |
| 2010-10-12 01:47 | cmlh_id_au | File Added: Cross_Site_Scripting_(XSS)_-_Reflected_-_ UserRoles_Edition.html_-_inpadUserId_Parameter.jpg | |
| 2010-10-12 01:47 | cmlh_id_au | Issue Monitored: cmlh_id_au | |
| 2010-10-25 08:56 | alostale | Assigned To | alostale => shuehner |
| 2010-10-25 08:56 | alostale | Status | new => scheduled |
| 2012-02-20 11:20 | shuehner | Assigned To | shuehner => alostale |
| 2012-02-22 15:52 | alostale | Relationship added | blocks 0019842 |
| 2012-02-22 15:54 | alostale | OBNetwork customer | => No |
| 2012-02-22 15:54 | alostale | Type | defect => design defect |
| 2012-09-24 23:25 | AugustoMauch | Note Added: 0052466 | |
| 2012-09-24 23:25 | AugustoMauch | Priority | normal => high |
| 2017-03-31 14:36 | alostale | Status | scheduled => acknowledged |
| 2017-04-10 14:34 | alostale | Assigned To | alostale => platform |
| 2022-02-01 08:08 | alostale | Assigned To | platform => Triage Platform Base |